Sustain requests: To get the most away from a DDoS assault, the superior variety of requests and overpowering site visitors want to carry on as time passes.
Though those methods are confused, balancers are loaded. Protocol attacks often contain manipulating traffic at levels three and 4 of the OSI/RM (the community and transportation levels, respectively). This is the next most popular sort of DDoS assault.
Rate limiting Yet another way to mitigate DDoS attacks should be to Restrict the quantity of requests a server can accept in just a certain time period. This on your own is usually not ample to combat a more subtle assault but may possibly serve as a component of a multipronged solution.
One of many realities of cybersecurity is that the majority of attackers are reasonably proficient people who have somehow figured out how to manipulate a specific community condition or scenario.
The Memcached company is a reputable service usually utilized to assist increase World wide web applications. Attackers have generally exploited Memcached implementations that aren't correctly secured, and perhaps those who are working adequately.
Normally deployed to control legit targeted traffic, load balancing servers will also be accustomed to thwart DDoS assaults. IT professionals can utilize these devices to deflect visitors clear of particular methods whenever a DDoS attack is under way.
Mazebolt Worldwide List of DDoS Attacks: This useful resource provides a working listing of attacks with data for example day, state of origin, downtime, assault details and in many cases links to push information regarding the incident.
Automated applications and AI in many cases are applied as helpers, but frequently companies need to have a talented IT Experienced to differentiate in between legit site visitors plus a DDoS attack.
How to prevent DDoS assaults Just before a cyberthreat is on the radar, you’ll want web ddos to possess a approach for just one in position. Preparedness is vital to promptly detecting and remedying an assault.
Conduct mock physical exercises for DDoS assaults. This might contain prepared or shock routines to correctly teach IT execs, workers and administration on response actions.
It is meant to aid people better know how DDoS attacks function And just how to shield their techniques from these types of assaults.
Therefore, There exists a smaller probability for safety analysts to detect this visitors and take care of it for a signature to disable a DDoS attack.
Burst Assault: Waged more than an incredibly short time period, these DDoS attacks only last a moment or perhaps a several seconds.
Load far more… Enhance this site Increase an outline, picture, and backlinks on the ddos-assault-equipment subject site in order that builders can more quickly study it. Curate this subject matter
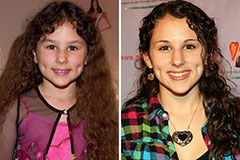 Hallie Eisenberg Then & Now!
Hallie Eisenberg Then & Now! Judge Reinhold Then & Now!
Judge Reinhold Then & Now! Joshua Jackson Then & Now!
Joshua Jackson Then & Now!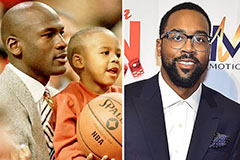 Marcus Jordan Then & Now!
Marcus Jordan Then & Now!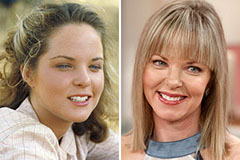 Melissa Sue Anderson Then & Now!
Melissa Sue Anderson Then & Now!